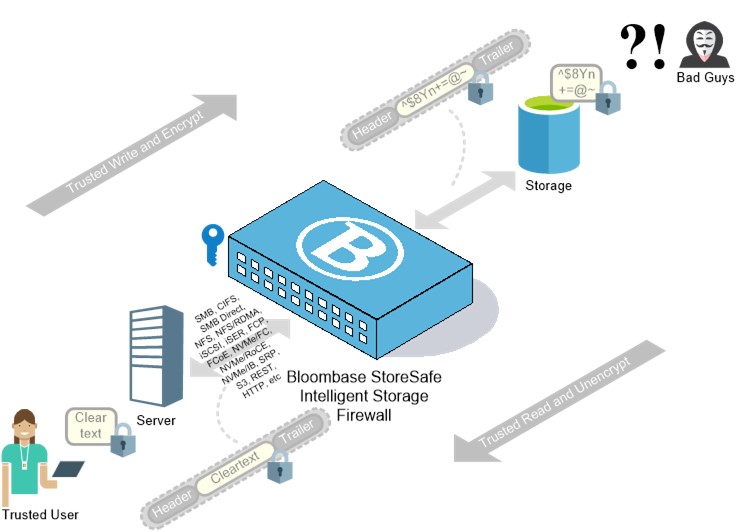
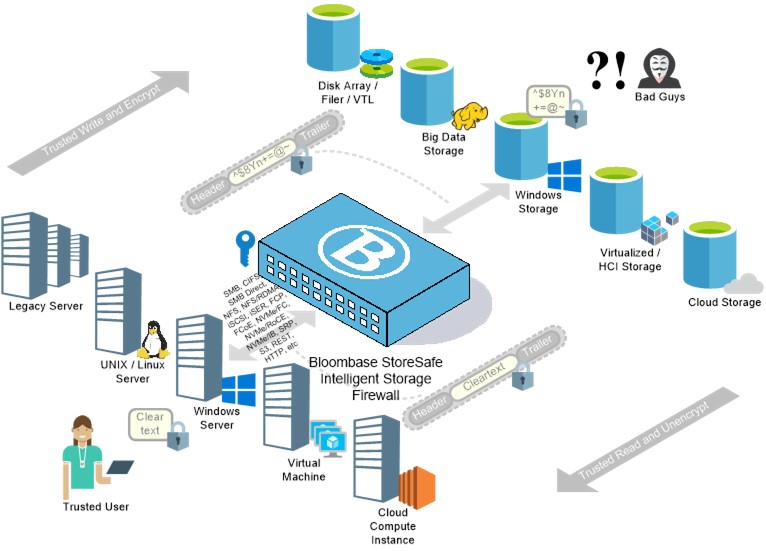
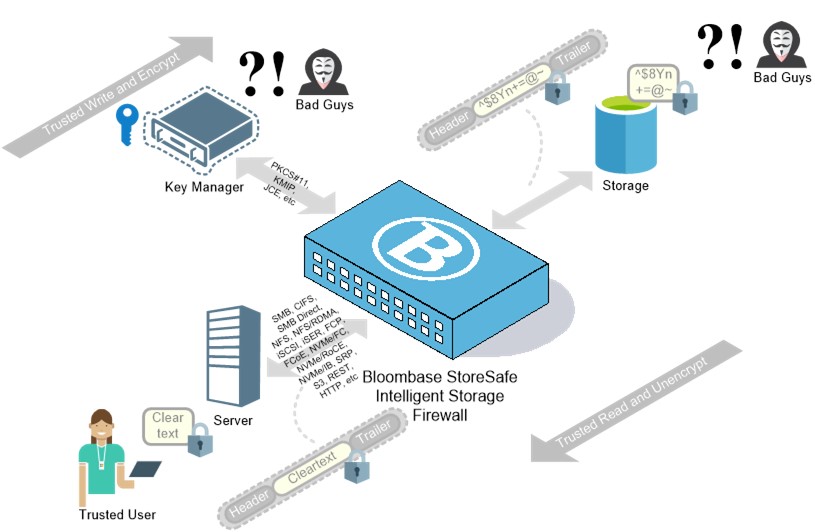
Product – Bloombase
© Copyright 2012 - 2025 | Avada Theme by ThemeFusion | All Rights Reserved | Powered by WordPress
AVADA IT
Fusce ut ipsum tincidunt, porta nisl sollicitudin, vulputate nunc. Cras commodo leo ac nunc convallis ets efficitur.
RECENT TWEETS
CONTACT US
12345 North Main Street,
New York, NY 5555551.800.555.6789
support@yoursite.com